Arpmess
HA = Hardware address aka mac address
PA = Protocol address (ipv4 in our case)
MITM = man in the middle
ARP (Address Resolution Protocol) is an OSI layer 2/3 protocol which links ipv4 addresses to mac addresses in local network.
In ipv6 network, ARP has been replaced by NDP (insecure by default) but security extension can be apply on top of the protocol to harden it against attacks.
In ARP, there are 2 packets type:
-
request, which are sent on the broadcast (to everyone)
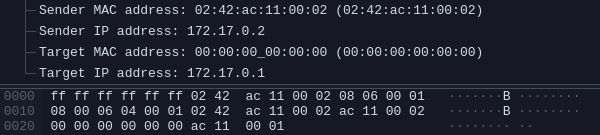
-
response, which are sent back to the demander
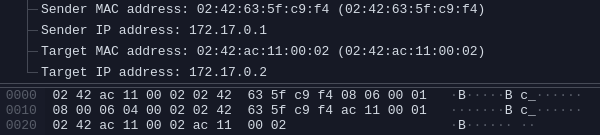
(on the example below, 172.17.0.1 is the gateway)
In this case 172.17.0.2 asked the whole network if someone owns the HA of 172.17.0.1.
172.17.0.1 himself respond: “yes i have 172.17.0.1, it’s located at 02:42:63:5f:c9:f4”
172.17.0.2 now knows the HA of 172.17.0.1 and can communicate with him, to, as an example, make DNS or HTTP requests ! (since it’s the gateway)
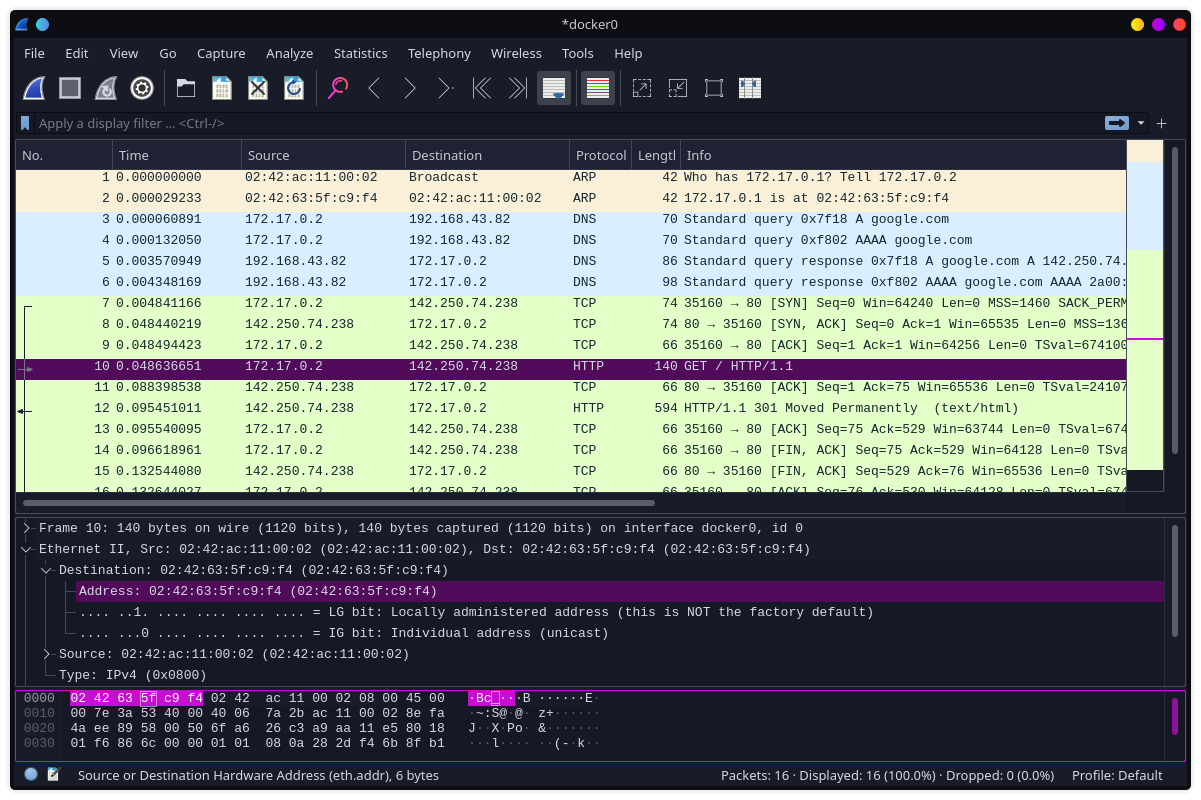
During a school project, i was tasked to explore the arp protocol and discover man in the middle attack by poisonning arp table.
The programm needed to behave as follows:
- take as arguments an ip and a mac address to spoof and an ip and a mac address of a victim (which will be poisoned)
- find an interface to bind a raw socket to
- wait for the victim to send an arp requests packet for a PA to spoof
- reply with the spoofed HA and exit
- it may only respond to that host
- it may only send a single arp reply
- use getifaddr(), sendto(), recvfrom()
The task was annoying to do for many reasons, mac address of the remote hosts needed to be known, only allowed to send 1 arp reply packet. Not many allowed function etc...
Which is why during my holidays i decided to develop arpmess an all in one arpsoof programm.
It can poison one or many host(s) arp table to intercept network traffic, deny internet access and so one…
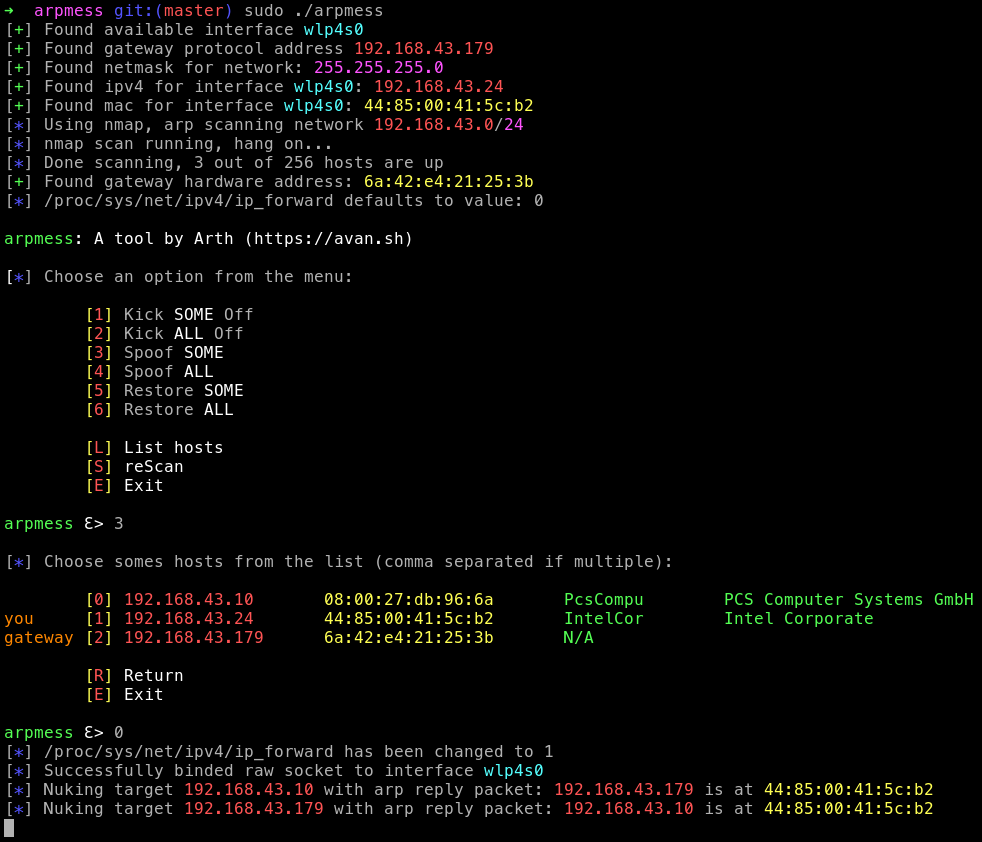
Here are a few example commands:
- specify interface (usb0) and gateway (192.168.43.17) to use, kicking 192.168.43.10 off the network
$ sudo ./arpmess -i usb0 -g 192.168.43.17 -t 192.168.43.10 -m kick
- sniff communication between 192.168.43.23 and the gateway, sending 120 arp packets per minute
$ sudo ./arpmess -t 192.168.43.23 -m spoof -p 120
- set the network mask to 255.255.224.0 and run in interactive mode
$ sudo ./arpmess -n 19
To get more infos about how the attack work, i recommand you checking out this function (in arpmess source code)
Thanks for reading, have fun with the tool, don’t hesitate to contribute or give me ideas !